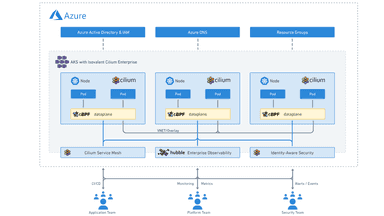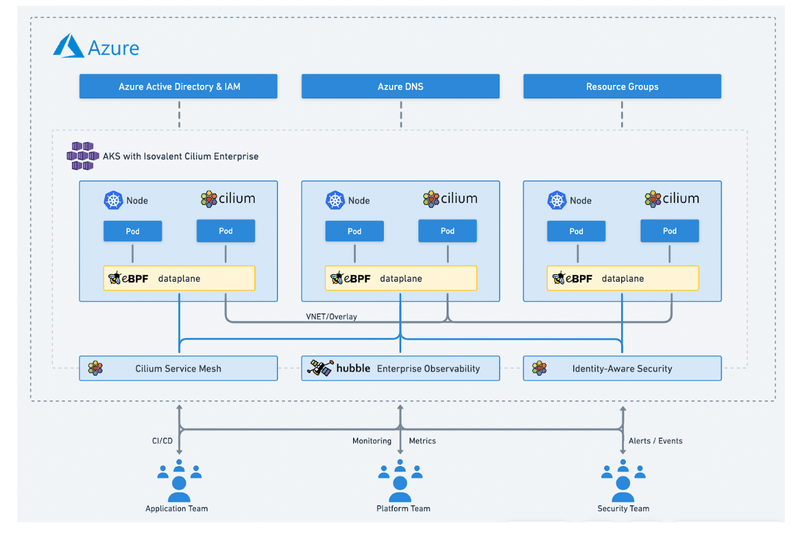
A few weeks ago, we announced that Isovalent Enterprise for Cilium is now available to Azure Kubernetes Service (AKS) customers as a one-click upgrade in the Microsoft Azure Marketplace and provide the full set of advanced Cilium features available to Azure customers. Today, in this tutorial, you will learn how to deploy Isovalent Enterprise for Cilium on your AKS cluster using Azure Marketplace, Azure CLI, and Azure Resource Manager (ARM) templates. The tutorial will walk through installing a new cluster and how to upgrade an existing AKS cluster running Azure CNI powered by Cilium to Isovalent Enterprise for Cilium.
What is Isovalent Enterprise for Cilium?
Isovalent Enterprise for Cilium is an enterprise-grade, hardened distribution of open-source projects Cilium, Hubble, and Tetragon, built and supported by the Cilium creators. Cilium enhances networking and security at the network layer, while Hubble ensures thorough network observability and tracing. Tetragon ties it all together with runtime enforcement and security observability, offering a well-rounded solution for connectivity, compliance, multi-cloud, and security concerns.
Why Isovalent Enterprise for Cilium?
For enterprise customers requiring support and usage of Advanced Networking, Security, and Observability features, “Isovalent Enterprise for Cilium” is recommended with the following benefits:
- Advanced network policy: Isovalent Cilium Enterprise provides advanced network policy capabilities, including DNS-aware policy, L7 policy, and deny policy, enabling fine-grained control over network traffic for micro-segmentation and improved security.
- Hubble flow observability + User Interface: Isovalent Cilium Enterprise Hubble observability feature provides real-time network traffic flow, policy visualization, and a powerful User Interface for easy troubleshooting and network management.
- Multi-cluster connectivity via Cluster Mesh: Isovalent Cilium Enterprise provides seamless networking and security across multiple clouds, including public cloud providers like AWS, Azure, and Google Cloud Platform, as well as on-premises environments.
- Advanced Security Capabilities via Tetragon: Tetragon provides advanced security capabilities such as protocol enforcement, IP and port whitelisting, and automatic application-aware policy generation to protect against the most sophisticated threats. Built on eBPF, Tetragon can easily scale to meet the needs of the most demanding cloud-native environments.
- Service Mesh: Isovalent Cilium Enterprise provides sidecar-free, seamless service-to-service communication and advanced load balancing, making deploying and managing complex microservices architectures easy.
- Enterprise-grade support: Isovalent Cilium Enterprise includes enterprise-grade support from Isovalent’s experienced team of experts, ensuring that any issues are resolved promptly and efficiently. Additionally, professional services help organizations deploy and manage Cilium in production environments.
This offering brings complete flexibility regarding access to Cilium features while retaining the advantageous ease of use and seamless integration with Azure. There are three ways to deploy Isovalent Enterprise for Cilium:
- Azure Marketplace
- Azure ARM Template
- Azure CLI
Why Azure Marketplace?
Azure Marketplace is an online store that contains thousands of IT software applications and services built by industry-leading technology companies. In Azure Marketplace, you can find, try, buy, and deploy the software and services needed to build new solutions and manage your cloud infrastructure. The catalog includes solutions for different industries and technical areas, free trials, and consulting services from Microsoft partners. Included among these solutions are Kubernetes application-based container offers. These offers contain applications that are meant to run on Kubernetes clusters such as Azure Kubernetes Service (AKS).
Pre-Requisites
The following prerequisites need to be taken into account before you proceed with this tutorial:
- An Azure account with an active subscription- Create an account for free
- AKS Cluster is up and running with Azure CNI powered by Cilium using either of the two options:
- The cluster can be created by Assigning IP addresses from an overlay network
- The cluster can be created by Assigning IP addresses from a virtual network
- Azure CLI version 2.41.0 or later. Run
az --versionto see the currently installed version. If you need to install or upgrade, see Install Azure CLI. - If using ARM templates or the REST API, the AKS API version must be 2022-09-02-preview or later.
- The kubectl command line tool is installed on your device. The version can be the same as or up to one minor version earlier or later than the Kubernetes version of your cluster. For example, if your cluster version is 1.26, you can use kubectl version 1.25, 1.26, or 1.27 with it. To install or upgrade kubectl, see Installing or updating kubectl.
- Isovalent Enterprise for Cilium as a marketplace extension is currently supported only in the following regions.
- Isovalent Enterprise for Cilium cannot be installed on AKS clusters created with Service Principals.
- It would be best if you upgraded your AKS clusters to managed identities.
- You must ensure that the following network and FQDN/application rules are required for AKS cluster extensions to work seamlessly.
- In the case of a private AKS cluster, configure rules to access an Azure container registry behind a firewall. The endpoints could be:
- REST endpoints.
- Dedicated data endpoints.
- Example:
arcmktplaceprod.centralindia.data.azurecr.io
- Example:
- Registry FQDN’s.
- If you upgrade your AKS cluster from Azure CNI powered by Cilium to Isovalent Enterprise for Cilium and the cluster has a lot of configuration, contact Isovalent support. They can assist you by setting “AgentOperationTimeoutInMinutes” to a reasonable value so that the upgrade can proceed.
- New namespace being created:
- When an AKS cluster is either being created or upgraded to Isovalent Enterprise for Cilium, it results in the creation of an additional namespace
azure-extensions-usage-system. Make sure that your Azure Policy whitelists this namespace. - When hubble is installed, it creates pods in the kube-system namespace by default. If you have an SIEM like Microsoft Defender, you can see an error similar to “New container ‘hubble-relay’ in the kube-system namespace detected.”
- It is an ideal installation process for Cilium and Hubble components. With the default alerting rules, these errors are expected. Cilium and Hubble’s components use best practices to run within the kube-system namespace within the cluster.
- Adding an exception for such events to Microsoft Defender’s alerting rules can help mitigate the errors. For such modifications, you can contact Microsoft Support. This is true for any alternative External Attack Surface Management tools.
- When an AKS cluster is either being created or upgraded to Isovalent Enterprise for Cilium, it results in the creation of an additional namespace
Register resource providers
Before you deploy a container offer, you must register with Microsoft.ContainerService and Microsoft.KubernetesConfiguration providers on your subscription by using the az provider register command:
Create a new AKS cluster with Isovalent Enterprise for Cilium
- In the Azure portal, search for Marketplace on the top search bar. In the results, under Services, select Marketplace.
- You can search for an offer or publisher directly by name or browse all offers. To find Kubernetes application offers, select Containers on the left side under Categories.

- Type “Isovalent” in the search window and select the offer.

- On the Plans + Pricing tab, select an option. Ensure that the terms are acceptable, and then select Create.
- Select the respective subscription in which the new AKS cluster needs to be created.
- Select the resource group in which to deploy the cluster. If a resource group doesn’t exist, click “Create New.”
- Click Create New Dev Cluster, select “Yes,” and click Next: Cluster Details.

- Provide a name for the AKS cluster and click “Next: Review + Create”

- Once Final validation is complete, click “Create”

- When the application is deployed, the portal will show “Your deployment is complete,” along with deployment details.

- Check the extensions installed on the cluster from Azure Portal. On the AKS cluster, navigate to the “Extensions + applications” menu to verify the same.

- Verify the deployment by using the following command to list the extensions that are running on your cluster:
- Log in to the Azure portal, browse Kubernetes Services, select the respective Kubernetes service created ( AKS Cluster), and click connect. This will help you connect to your AKS cluster and set the individual Kubernetes context.
- Validate the version of Isovalent Enterprise for Cilium on your newly created cluster
Note– cee-indicates Cilium Enterprise Edition, the Enterprise Version of Cilium offered by Isovalent, installed on the cluster.
Upgrade an existing cluster.
Note-
- You can upgrade an existing AKS cluster running Azure CNI powered by Cilium in the same region from where the upgrade is being attempted. The cluster being upgraded can be running Azure CNI powered by Cilium using either of the two options:
- The cluster can be created by Assigning IP addresses from an overlay network
- The cluster can be created by Assigning IP addresses from a virtual network
- The version on your cluster can be verified by:
Preparing for the upgrade
This section will guide you through the steps required to upgrade an existing AKS cluster running Azure CNI powered by Cilium to Isovalent Enterprise for Cilium.
- In the Azure portal, search for Marketplace on the top search bar. In the results, under Services, select Marketplace.
- You can search for an offer or publisher directly by name or browse all offers. Select Containers on the left side under Categories to find Kubernetes application offers.

- Type “Isovalent” In the search window and select the offer.

- On the Plans + Pricing tab, select an option. Ensure that the terms are acceptable, and then select Create.
- Select the resource group in which the cluster exists that we will be upgraded.
- Click Create New Dev Cluster, select “No,” and click Next: Cluster Details.

- As “No” was selected, this will result in an upgrade of an already existing cluster in that region
- The name for the AKS cluster will be auto-populated by clicking on the drop-down selection.
- Click “Next: Review + Create” Details.

- Once Final validation is complete, click “Create”

- When the application is deployed, the portal will show “Your deployment is complete,” along with deployment details.

- Check the extensions installed on the cluster from Azure Portal. On the AKS cluster, navigate to the “Extensions + applications” menu to verify the same.

- Verify the deployment by using the following command to list the extensions that are running on your cluster:
- Log in to the Azure portal, browse Kubernetes Services, select the respective Kubernetes service created ( AKS Cluster), and click connect. This will help you connect to your AKS cluster and set the respective Kubernetes context.
- Validate the version of Isovalent Enterprise for Cilium on your newly upgraded cluster
Note– cee-indicates Cilium Enterprise Edition, the Enterprise Version of Cilium offered by Isovalent, to which the cluster was upgraded.
Manage the offer lifecycle
For lifecycle management, an Azure Kubernetes offer is represented as a cluster extension for AKS. For more information, see Cluster extensions for AKS.
Purchasing an offer from Azure Marketplace creates a new extension instance on your AKS cluster. View the extension instance from the cluster by using the following command:
Note– extension-name, in this case, is cilium
Remove an offer
You can delete a purchased plan for an Azure container offer by deleting the extension instance on the cluster. For example:
Installation via Azure Resource Manager (ARM) Template
Since moving to the cloud, many teams have adopted agile development methods. These teams iterate quickly, need to repeatedly deploy their solutions to the cloud, and know their infrastructure is reliable.
You can use Azure Resource Manager (ARM) templates to implement infrastructure as code for your Azure solutions. The template is a JavaScript Object Notation (JSON) file that defines the infrastructure and configuration for your project. The template uses declarative syntax, which lets you state what you intend to deploy without writing the sequence of programming commands to create it. In the template, you specify the resources to deploy and the properties for those resources.
To deploy a Kubernetes application programmatically through ARM templates, a user needs to select the Kubernetes application and settings, generate an ARM template, accept legal terms and conditions, and finally deploy the ARM template.
Pre-Requisites
The following prerequisites need to be taken into account before you proceed with this tutorial:
- An Azure account with an active subscription- Create an account for free
- AKS Cluster is up and running with Azure CNI powered by Cilium using either of the two options:
- The cluster can be created by Assigning IP addresses from an overlay network
- The cluster can be created by Assigning IP addresses from a virtual network
- Azure CLI version 2.41.0 or later. Run az –version to see the currently installed version. If you need to install or upgrade, see Install Azure CLI.
- Templates are JavaScript Object Notation (JSON) files. To create templates, you need a good JSON editor. We recommend Visual Studio Code with the Azure Resource Manager Tools extension. If you need to install these tools, see Quickstart: Create ARM templates with Visual Studio Code.
- The kubectl command line tool is installed on your device. The version can be the same as or up to one minor version earlier or later than the Kubernetes version of your cluster. For example, if your cluster version is 1.26, you can use kubectl version 1.25, 1.26, or 1.27 with it. To install or upgrade kubectl, see Installing or updating kubectl.
- You must ensure that the following network and FQDN/application rules are required for AKS cluster extensions to work seamlessly.
- Isovalent Enterprise for Cilium cannot be installed on AKS clusters created with Service Principals.
- It would be best if you upgraded your AKS clusters to managed identities.
- In the case of a private AKS cluster, configure rules to access an Azure container registry behind a firewall. The endpoints could be:
- REST endpoints.
- Dedicated data endpoints.
- Example:
arcmktplaceprod.centralindia.data.azurecr.io
- Example:
- Registry FQDN’s.
- If you upgrade your AKS cluster from Azure CNI powered by Cilium to Isovalent Enterprise for Cilium and the cluster has many configurations, contact Isovalent support. They can assist you by setting “AgentOperationTimeoutInMinutes” to a reasonable value so that the upgrade can proceed.
- New namespace being created:
- When an AKS cluster is either being created or upgraded to Isovalent Enterprise for Cilium, it results in the creation of an additional namespace
azure-extensions-usage-system. Make sure that your Azure Policy whitelists this namespace. - When hubble is installed, it creates pods in the kube-system namespace by default. If you have an SIEM like Microsoft Defender, you can see an error similar to “New container ‘hubble-relay’ in the kube-system namespace detected.”
- It is an ideal installation process for Cilium and Hubble components. With the default alerting rules, these errors are expected. Cilium and Hubble’s components use best practices to run within the kube-system namespace within the cluster.
- Adding an exception for such events to Microsoft Defender’s alerting rules can help mitigate the errors. For such modifications, you can contact Microsoft Support. This is true for any alternative External Attack Surface Management tools.
- When an AKS cluster is either being created or upgraded to Isovalent Enterprise for Cilium, it results in the creation of an additional namespace
Register resource providers
Before you deploy a container offer, you must register the Microsoft.ContainerService and Microsoft.KubernetesConfiguration providers on your subscription by using the az provider register command:
Select Kubernetes Application
First, select the Kubernetes application you want to deploy/upgrade in the Azure portal.
- In the Azure portal, search for Marketplace on the top search bar. In the results, under Services, select Marketplace.
- You can search for an application or publisher directly by name or browse all applications. To find Kubernetes application applications, on the left side, under Categories, select Containers.

Generate ARM Template
- Type “Isovalent” in the search window and select the application.

- On the Plans + Pricing tab, select an option. Ensure that the terms are acceptable, and then select Create.
- Select the respective subscription in which the existing AKS cluster has already been created with Azure CNI powered by Cilium.
- Select the resource group to deploy the cluster in.
- Click Create New Dev Cluster, select “No,” and click Next: Cluster Details.

Note: To create a new AKS cluster, click on the resource group and select “Create New” under Resource Group. Also, to create a new cluster with Isovalent Enterprise for Cilium, select “Yes” at the “Create new dev cluster” step.
- The AKS cluster name will be available through the drop-down. Click on “Next: Review + Create.”

- Once Final validation is complete, click > “View Automation Template” > click “Download”


- You’ll see the ARM template in the editor if all the validations have passed.

- Download the ARM template and save it to a location on your computer.
- You need to note the following values, which will be used later in this tutorial.
Plan-publisher
Plan-offerIDandPlan-name
- You need to exit the Azure portal screen and not Click on Create in the UI workflow, as ARM templates will now install the “Cilium” extension and enable the Enterprise features.
Editing the json file
- Unzip the ARM template file, which will include a parameters.json file, and edit the following fields:
- ClusterResourceName– The description should be the name of the AKS cluster that is either being created or an existing AKS cluster running on Azure CNI powered by Cilium.
- createNewCluster- The default value is false, meaning an existing AKS cluster is running on Azure CNI powered by Cilium, which will be upgraded to Isovalent Enterprise for Cilium. The user can turn it to True if they are creating a new cluster on Isovalent Enterprise for Cilium.
- extensionResourceName– The description should be the cilium extension and not be edited.
- Location- A description of the location of the AKS resource should be the location where the AKS resource was created/ upgraded.
Accept terms and agreements
Before deploying a Kubernetes application, you must accept its terms and agreements. To do so, use Azure CLI or Azure PowerShell. We will use Azure CLI to deploy the ARM template for this tutorial.
Be sure to use the values you copied before downloading the ARM template for plan-publisher, plan-offerID, and plan-name in your command.
Values.yaml to enable Enterprise Features
- To enable Enterprise features, you can create a sample yaml file as shown in the example below:
Setting Enterprise Values for the ARM Template
- You can download yq and inject custom helm values into the ARM template, as Azure ARM templates follow a
key:valuepair syntax notation.- Users can also use a tool of their choice to inject Helm values.
- This output will be a JSON file that will be used to deploy the ARM template. The sample JSON file would look like the one below, which you must copy.
Note– The output below is truncated.
Deploy ARM Template
- Sign in with your Azure credentials in Azure CLI to start working with ARM templates.
- Choose the subscription you want to use if you have multiple Azure subscriptions.
- Replace
SubscriptionNamewith your subscription name. - You can also use your subscription ID instead of your subscription name.
- Replace
- To deploy the template, use either Azure CLI or Azure PowerShell. Use the resource group you created while creating the cluster on Azure CNI powered by Cilium.
- Template-File type is “json.”
- The deployment command returns results. Look for
ProvisioningStateto see whether the deployment succeeded.
Note– The output below is truncated.
Verify Deployment
- You can verify the deployment by exploring the resource group from the Azure portal.
- Sign in to the Azure portal.
- From the left menu, select Resource Groups.
- Check the box to the left of the resource group where the AKS cluster resides.
- Select the resource group you used in the earlier procedure.
- Check the extensions installed on the cluster from the Azure Portal. Then, go to the “Extensions + applications” menu on the AKS cluster to verify the settings.

- Optional– Log in to the Azure portal, browse to Kubernetes Services>, select the respective Kubernetes service created ( AKS Cluster), and click connect. This will help you connect to your AKS cluster and set the respective Kubernetes context.
- Verify the deployment by using the following command to list the extension and features that were enabled on your cluster after the successful deployment of the ARM template:
- Validating the version of Isovalent Enterprise for Cilium on your newly created cluster
Installation via Azure CLI
A user can create extension instances in an AKS cluster, setting required and optional parameters,, including options related to updates and configurations. Users can also view, list, update, and delete extension instances.
Pre-Requisites
The following prerequisites need to be taken into account before you proceed with this tutorial:
- An Azure subscription.
- While creating the extension- Users need to make sure that they have an AKS Cluster up and running with Azure CNI powered by Cilium
- The cluster can be created by Assigning IP addresses from an overlay network
- The cluster can be created by Assigning IP addresses from a virtual network
- While updating the extension- Users need to ensure they have an AKS Cluster up and running with Isovalent Enterprise for Cilium from the Azure marketplace.
- Isovalent Enterprise for Cilium as a marketplace extension is currently supported only in the following regions.
- You must ensure that the following network and FQDN/application rules are in place for AKS cluster extensions to work seamlessly.
- Isovalent Enterprise for Cilium cannot be installed on AKS clusters created with Service Principals.
- You need to upgrade your AKS clusters to managed identities.
- In the case of a private AKS cluster, configure rules to access an Azure container registry behind a firewall. The endpoints could be:
- REST endpoints.
- Dedicated data endpoints.
- Example:
arcmktplaceprod.centralindia.data.azurecr.io
- Example:
- Registry FQDN’s.
- If you are upgrading your AKS cluster from Azure CNI powered by Cilium to Isovalent Enterprise for Cilium and the cluster has a lot of configuration, make sure you get in touch with Isovalent support. They can assist you by setting “AgentOperationTimeoutInMinutes” to a reasonable value so that the upgrade can proceed.
- New namespace being created:
- When an AKS cluster is either being created or upgraded to Isovalent Enterprise for Cilium, it results in the creation of an additional namespace
azure-extensions-usage-system. Make sure that your Azure Policy whitelists this namespace. - When hubble is installed, it creates pods in the kube-system namespace by default. If you have an SIEM like Microsoft Defender, you can see an error similar to “New container ‘hubble-relay’ in the kube-system namespace detected.”
- It is an ideal installation process for Cilium and Hubble components. With the default alerting rules, these errors are expected. Cilium and Hubble’s components use best practices to run within the kube-system namespace within the cluster.
- Adding an exception for such events to Microsoft Defender’s alerting rules can help mitigate the errors. For such modifications, you can contact Microsoft Support. This is true for any alternative External Attack Surface Management tools.
- When an AKS cluster is either being created or upgraded to Isovalent Enterprise for Cilium, it results in the creation of an additional namespace
- The
Microsoft.ContainerServiceandMicrosoft.KubernetesConfigurationResource providers must be registered with your subscription. - To register these providers, run the following command:
- The latest version of the
k8s-extensionAzure CLI extensions. Install the extension by running the following command:
- If the extension is already installed, make sure you’re running the latest version by using the following command:
Select the Kubernetes application
You must select the Kubernetes application they want to deploy in the Azure portal and copy some of the details for later use.
- In the Azure portal, go to the Marketplace page.
- Select the Kubernetes application.
- Select the required plan.
- Select the Create button.
- Fill out all the application (extension) details.
- In the Review + Create tab, select Download a template for automation. If all the validations are passed, the ARM template will appear in the editor.
- Examine the ARM template:
- In the variables section, copy the
plan-name,plan-publisher,plan-offerID, andclusterExtensionTypeNamevalues for later use. - In the resource
Microsoft.KubernetesConfiguration/extensions‘ section, copy theconfigurationSettingssection for later use.
- In the variables section, copy the
Accept terms and agreements
- Before deploying a Kubernetes application, you must accept its terms and agreements. To do so, use Azure CLI or Azure PowerShell. This section will use Azure CLI to deploy the ARM template.
- Be sure to use the values you copied before downloading the ARM template for
plan-publisher,plan-offerID, andplan-namein your command.
Setting the correct Context
Log in to the Azure portal, browse to Kubernetes Services, select the respective Kubernetes service created ( AKS Cluster), and click on connect. This will help you connect to your AKS cluster and set the respective Kubernetes context.
Creating the extension
You can create a new extension instance with k8s-extension create passing values for the mandatory parameters.
Update the extension
You can update an existing extension (Cilium) installed on an AKS cluster with Isovalent Enterprise for Cilium.
- Listing an existing extension
Enabling Enterprise Features
- You will be prompted for a prompt while enabling these features; select Yes.
Verifying the extension
Verify the k8s-extension using the following command to list the extensions and features enabled on your cluster using Azure CLI.
Validation-Isovalent Enterprise for Cilium
Cluster and Cilium Health Check
- Check the nodes’ status and ensure they are in a “Ready” state
cilium-health, which is a tool available in Cilium that provides visibility into the overall health of the cluster’s networking connectivity. Usecilium-healthto get visibility into the overall health of the cluster’s networking connectivity.
Cilium Connectivity Test
- Run
cilium connectivity test(an automated test that checks that Cilium has been deployed correctly and tests intra-node connectivity, inter-node connectivity, and network policies) to verify that everything is working as expected.
How can you downgrade from one Enterprise release to another?
- If there is a requirement to downgrade the respective
CNABversion, you can use Azure CLI commands to achieve the desired result.- example scenario to downgrade to the CNAB version 1.1.41, which corresponds to the Cilium Enterprise version
1.13.20-cee.1.
- example scenario to downgrade to the CNAB version 1.1.41, which corresponds to the Cilium Enterprise version
- Since the auto upgrade minor version is set to true by default, it will lead to a failure, and an upgrade will not be allowed, so you need to turn off the ‘
upgrade minor version‘ flag.
Troubleshooting
You can always refer to this article on troubleshooting errors when deploying cluster extensions for Azure Kubernetes Service (AKS).
Conclusion
Hopefully, this post gave you a good overview of deploying Isovalent Enterprise for Cilium in your AKS clusters. If you have any feedback on the solution, please share it with us. You’ll find us on the Cilium Slack channel.
Try it out
- Isovalent Enterprise for Cilium on the Azure marketplace.
Further Reading
- Tutorial on installing an AKS cluster running Azure CNI powered by Cilium
- Azure and Isovalent main partner page

Amit Gupta is a senior technical marketing engineer at Isovalent, powering eBPF cloud-native networking and security. Amit has 22+ years of experience in Networking, Telecommunications, Cloud, Security, and Open-Source. He has previously worked with Motorola, Juniper, Avi Networks (acquired by VMware), and Prosimo.io (acquired by Palo Alto Networks). He is keen to learn and try out new technologies that aid in solving day-to-day problems for operators and customers.
He has worked in the Indian start-up ecosystem for a long time and helps new folks in that area outside of work. Amit is an avid runner and cyclist, and also spends considerable time helping kids in orphanages.