Imagine navigating a bustling city on foot. While understanding traffic rules is essential, wouldn’t it be easier to have a visual map guiding your way? This is precisely the advantage offered by the Network Policy Editor.
Historically, abstracting complexity has proven to enhance user experience and adoption. The Network Policy Editor embraces this principle by removing the hassle associated with crafting Network Policies. Now, operators can focus on their core objective: creating efficient network policies to secure communication in their Kubernetes clusters.
In the first and second parts of this series, we explored Cilium network policy, compared Cilium network policy to the standard Kubernetes network policy, and wrote network policies that implemented some common user stories. In this third part of the series, we will explore the Network Policy Editor.
Defining security policies is a crucial part of securing Kubernetes clusters, Kubernetes network policies provide a construct that defines how traffic is allowed to flow in and out of the various components in the cluster. However, the learning curve for Kubernetes network policies can be quite steep and there are many subtleties in the behavior network policies that take work to wrap your head around even for experienced users.
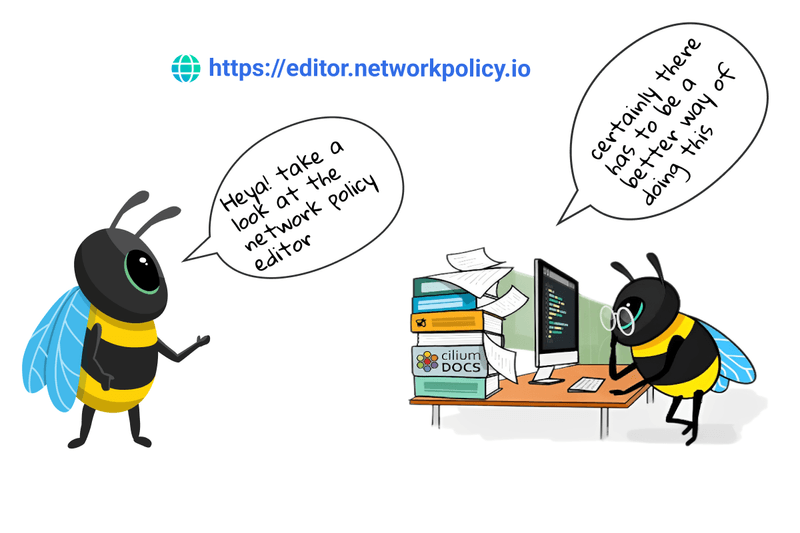
Enter the Network Policy Editor. The Network Policy Editor is a free tool designed to ease the cognitive overhead of developing network policies, the Network Policy Editor was built in response to alleviating some of the common challenges when working with and trying to understand and implement network policies.
Access the Network Policy Editor to get started.
What can the Network Policy Editor do?
- Interactive Policy Creation Assist
- Visualize Policy
- Translate between Kubernetes and Cilium network policy
- Upload Policy
- Download Policy
- Share Policy
- Policy Security Score
- Automatic Generation of Policies from Hubble flow logs
- Network Policy Tutorials
Interactive Policy Creation Assist
The Network Policy Editor features a guided tour for creating both Kubernetes and Cilium Network policy. Each section of the network policy resource is explained and input fields are provided for indicating the values of the relevant fields as opposed to manually wrangling fields in YAML files. This eliminates possible errors that can stem from incorrect YAML syntax and incorrect usage of the network policy spec definition.
Visualize Policy
The Network policy editor provides an intuitive UI for visualizing the rules and effects of a policy. The UI presents the policy and its rulesets in a visual way allowing users to edit the values for each rule on the UI.
Translate between Kubernetes and Cilium network policy
For the supported policy types, the Network policy UI can translate between the standard Kubernetes network policy resource and Cilium network policy resource. This can be used to ease the migration from Kubernetes network policy to Cilium network policy.
N/B: The network policy editor currently only supports translating rules that map one-to-one with both Cilium and Kubernetes network policies, this means features like layer 7 policies are not supported.
Upload Policy
Existing Kubernetes and Cilium network policy YAML files can be uploaded on the Network Policy Editor and users can then access every other feature the network policy editor provides such as policy visualization, policy scoring, etc. This feature can be used to better understand an existing policy you’ve written by hand, edit it, and validate it for correctness.
Click on the button with the Tooltip that says “Upload Policy YAML” to upload an existing policy to the editor.
Download Policy YAML File
When you’re done creating, editing, and understanding a policy, you can download the policy YAML file.
Click on the button that says “Download” to download the policy YAML file.
Share Policy via Github Gist
You can share a policy from the editor as a GitHub Gist
Click on the “Share” button and the Network Policy Editor will automatically write current policy YAML to GitHub Gist under your name and provide you with a link you can share. Network Policy Editor will request read/write permissions to your GitHub Gist to perform this operation.
Security Score
The Editor features the ability to check the security score of policies to understand the level of security they add to your cluster.
Click on the policy rating button to see the details of the score for your policy.
Network policy tutorials
The network policy editor features tutorial-styled content covering network policies and some of the subtleties associated with creating them accurately. Tutorials covering topics such as understanding empty selectors, misunderstanding how policy rules combine, cross-namespace traffic, etc., can be found in the editor. Click on the main tutorial button and select a tutorial from the list in the dropdown menu.
Generate Policies from Hubble flow logs
You can upload your Hubble flow logs to the network policy editor and it will analyze the flow logs and automatically generate network policies based on the observed network traffic.
Conclusion
We started this series by highlighting the risk absence of network segmentation controls can pose to Kubernetes clusters, drawing an analogy to a city with no traffic rules. We proceeded to introduce Cilium network policies as a solution to enforce robust network segmentation rules in Kubernetes. In the second part of this series, we delved deeper, exploring some common user stories that shed light on the practical implementation of Cilium network policies. These user stories showcased how Cilium empowers operators to enforce network traffic rules at the different levels of the OSI model.
Finally, in this third part of the series, we introduced the Network Policy Editor, your invaluable visual map and city planning tool. This free tool eases the cognitive overhead of writing Network Policies by offering features like uploading policies, visualizing them, editing them on the UI, downloading the policies, seeing the security rating for a policy, generating policies from Hubble flow logs, and sharing policies.
Check out Network Policy Editor and get started today!
If you have questions or feedback, reach out via the network policy channel in the Cilium Slack.
- Dive into Cilium using the hands-on lab, Getting Started with Cilium.
- Get hands-on practice with the Network policy lab.
- Try out the host policy feature with the Cilium Host Firewall lab.

Paul is a security-focused community builder at Isovalent – the company behind Cilium & Tetragon. Before joining Isovalent, Paul worked in the startup world as a backend and infrastructure-focused software engineer using various cloud-native technologies, including Kubernetes. Paul has also worked as a software engineering trainer, designing curriculum and content to train budding software engineers.
You can find Paul hanging out in various open-source communities and speaking at conferences like the Open Source Festival. Paul enjoys swimming, cycling, and mountain biking.