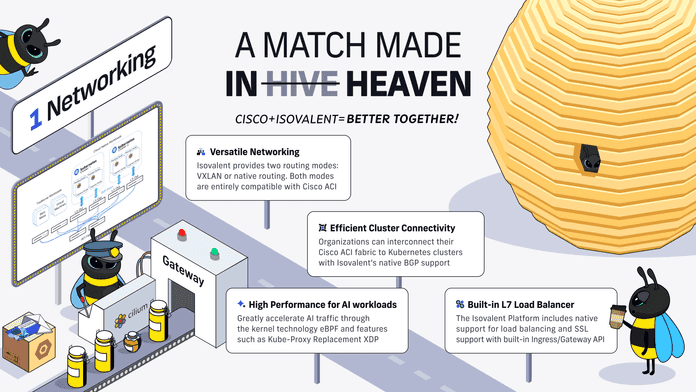
Isovalent & Cisco ACI: Better Together
In this blog post, learn why Isovalent and ACI work so well together to provide enhanced networking, security and observability for K8S!

In this blog post, learn why Isovalent and ACI work so well together to provide enhanced networking, security and observability for K8S!
This blog will guide you in enabling Isovalent Cluster Mesh across two Kubernetes clusters (GKE Data Plane v1) with different routing modes via Mixed Routing Mode.
How does Imagine Learning deliver a seemless end-user experience for their students? By implementing Cilium with Isovalent! Read the case study!
Isovalent Enterprise for Tetragon 1.15: CPU & Memory Metrics, Audit eBPF Operations, Advanced Filtering!
Learn about what 2025 has in store in the realms of eBPF, networking and security in the 2025 Isovalent predictions!
We are excited to announce the availability of the EC2 image builder integration for Isovalent Enterprise, which uses Tetragon as the underlying foundation, to streamline the deployment of Isovalent Enterprise via Amazon Machine Image (AMI) build processes.
We think, innovate, and breathe open source and we are fully committed to its principles and values.
Join our communityIn this blog post, learn how Cilium can overcome IP address exhaustion issues you may face in your Kubernetes clusters.
Use the MITRE ATT&CK framework to transform the deep telemetry from Tetragon into clear, actionable insights about adversary behavior.
Why do teams choose Isovalent as the unified data plane for highly scaled cloud security, networking, and observability?
This blog shows how to deploy a Red Hat OpenShift Service on an AWS (ROSA) cluster without a preinstalled CNI plugin and then add Isovalent Enterprise for Cilium as the CNI plugin. We also add the Red Hat OpenShift Virtualisation Operator and deploy VM's on the cluster.
Top 5 Runtime Security Risks for Financial Services CISOs (And How to Solve Them with Cilium & Tetragon)
In this wrap-up of KubeCon North America 2024, learn what we found special about this year's event in Salt Lake City!