In today’s constantly evolving cloud environments, deploying robust security measures is critical for maintaining a strong security posture. Tetragon is the standard for eBPF-based security observability and runtime enforcement and has seen massive adoption by platform and security teams globally. Its eBPF-based architectural approach provides unprecedented visibility into system activity while maintaining minimal performance overhead. Tetragon is especially difficult when operations have to scale rapidly. Amazon EC2 Image Builder is a game-changing solution that simplifies the deployment of Tetragon. We are excited to announce the availability of the EC2 image builder integration for Isovalent Enterprise, which uses Tetragon as the underlying foundation, to streamline the deployment of Isovalent Enterprise via Amazon Machine Image (AMI) build processes.
By integrating Tetragon into preconfigured “Golden AMIs,” Image Builder eliminates many common deployment challenges, enhances security, and allows teams to focus on leveraging insights rather than managing installations. This integration will enable users to quickly build EC2 instances with Tetragon and see how workload data can be correlated to actual network performance metrics, deep security insights, rapid troubleshooting, and managing operations costs in AWS environments using Tetragon.
What is Tetragon’s role in Cloud Security?
When customers have cloud native environments, they may face new challenges. They may find gaps in their network visibility as traffic moves to the cloud. It is also challenging to make sense of the vast volume of data once that visibility has been achieved. Tetragon provides a robust solution for these challenges with deep visibility into system behavior through eBPF-powered security observability. Tetragon captures granular security-significant data, prying into places out of reach for traditional security tooling. Security teams now have vast amounts of low-level telemetry-system calls, file accesses, network connections, and process events- all rich with security significance.

The new integration between Isovalent Enterprise and AWS pushes networking telemetry directly to Amazon CloudWatch Network Monitoring, where workload data can be correlated to actual network performance metrics in AWS environments. These insights can seamlessly integrate into Splunk, enabling network teams to build unified dashboards that consolidate metrics from on-premises networks, cloud networks, and application performance. In contrast, security teams can utilize this data for threat detection and policy enforcement. Enriching workload visibility data with AWS network performance and making it available to Splunk enables real-time visibility into the entire AWS network fabric. This gives network teams the observability and control they need to build and optimize truly agile environments that run today’s modern applications.
Without Tetragon, it can be difficult to distinguish between application issues and underlying network problems. The quicker and more efficiently Tetragon is deployed, the more effectively it can safeguard cloud workloads. However, traditional deployment methods often involve manual processes, which are time-consuming and prone to errors. This is where EC2 Image Builder shines.
How does the EC2 Image Builder simplify Deployment?
EC2 Image Builder offers a fully integrated platform for creating, managing, and deploying standardized Golden AMIs. This service addresses several operational challenges related to software deployment and security across cloud environments.
- One of the most significant benefits of EC2 Image Builder is standardization. Manually configuring instances can lead to discrepancies that undermine security and efficiency. With Image Builder, organizations can create preconfigured standardized images to meet specific requirements, reducing variability and ensuring consistency across deployments.
- Another key advantage is automation. Regular updates, including security patches, can be labor-intensive and disruptive if performed manually. Image Builder automates these processes, ensuring images remain current with minimal effort. Moreover, it integrates vulnerability scanning and compliance checks, providing an added layer of security before images are deployed.
- The service also handles complex dependency management. Different operating systems often require unique configurations, leading to compatibility issues. Image Builder eliminates this problem by taking a templated, version-controlled approach to image creation. This ensures software dependencies are met, configurations are consistent, and errors are minimized.
Capabilities like these translate into tangible benefits for organizations, including reduced operational costs, improved resource efficiency, and enhanced visibility. In addition, the service’s logging and versioning features provide greater control over image configurations and updates, simplifying troubleshooting and audit processes.
How can I enhance Tetragon Deployment with EC2 Image Builder?
For enterprises and businesses already using Tetragon or those exploring its capabilities, EC2 Image Builder addresses deployment challenges that can arise at scale. Consider a scenario where thousands of workloads are running Tetragon, and the operating systems on those servers are approaching the end of life. Without a solution like Image Builder, deploying Tetragon after upgrading the OS would require significant time and effort.
While traditional methods like user data scripts or configuration management tools can achieve similar outcomes, they have limitations. User data scripts require extensive testing to ensure accuracy and are often time-consuming. Configuration management tools automate deployment but demand ongoing maintenance to keep scripts updated and compatible across environments. EC2 Image Builder bypasses these complexities by embedding Tetragon into Golden AMIs. Each instance launched from these images is preconfigured with the necessary configuration, eliminating the need for additional deployment steps.
This streamlined process reduces operational overhead, ensures consistent security coverage, and allows cloud teams to focus on scaling operations rather than managing Tetragon installations.
How do you get started with EC2 Image Builder and Tetragon?
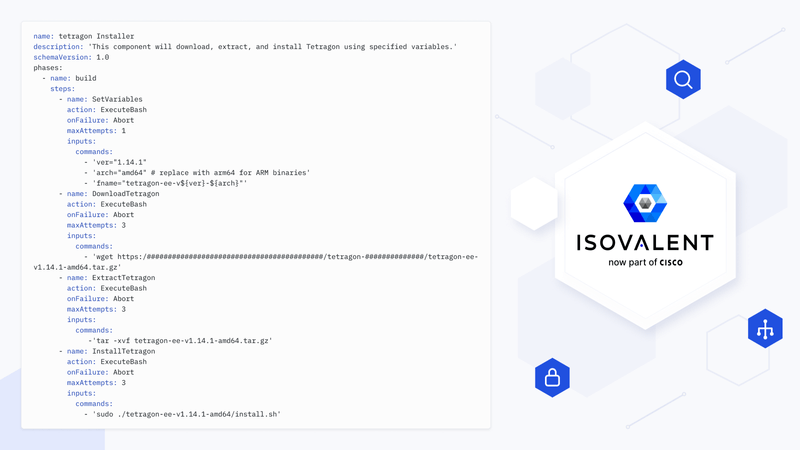
Once you subscribe to Tetragon from the AWS Marketplace, you only need to Click on > Launch on the EC Image Builder console. A YAML configuration file can define the integration parameters for Tetragon.

Here’s an example:
A Preemptive Approach to Cloud Security
Integrating EC2 Image Builder into your Tetragon deployment strategy ensures your cloud operations are future-proof. By automating Tetragon deployment, enterprises can maintain consistent security, efficiently scale to meet growing demands and reduce operational overhead. With Tetragon pre-installed in every instance, businesses benefit from immediate protection and eliminate monitoring gaps. This proactive approach transforms cloud security from a reactive, labor-intensive task into a streamlined and scalable solution. By leveraging EC2 Image Builder, your organization can create a more secure, efficient, and resilient cloud environment. We encourage you to explore Tetragon on the AWS Marketplace. Request a demo today if you want to learn more before starting. Click the button below to get in touch!
Suggested Reading
- AWS Marketplace now offers EC2 Image Builder components from independent software vendors
- A New Approach to Network Troubleshooting in the Multicloud World
- Tetragon in AWS Marketplace.
