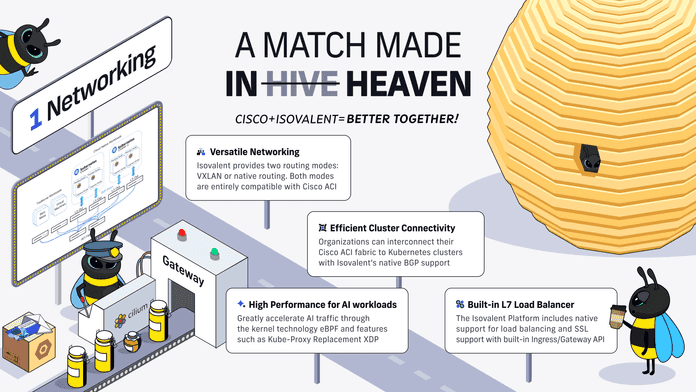
Isovalent & Cisco ACI: Better Together
In this blog post, learn why Isovalent and ACI work so well together to provide enhanced networking, security and observability for K8S!

In this blog post, learn why Isovalent and ACI work so well together to provide enhanced networking, security and observability for K8S!
With the help of Isovalent and Cilium, SBP were able to migrate PCI-DSS workloads.
Cilium 1.16 is out! Including Netkit for the veth replacement for high-performance networking, Gateway API GAMMA support, BGPv2 and more!
This article shows how to initially deploy an EKS cluster without a preinstalled CNI plugin and then add Cilium as the CNI plugin.
In this tutorial, you will learn how to enable Enterprise features in an Elastic Kubernetes Service (EKS) cluster running Isovalent Enterprise for Cilium.
In this blog post, we're looking at Cilium's support for netkit - a revolutionary Linux kernel networking technology.
We think, innovate, and breathe open source and we are fully committed to its principles and values.
Join our communityThis blog post will walk you through enabling multicast in the cloud with Cilium.
Isovalent Enterprise Dashboards for Cilium help reduce operational risk in your cloud native platforms by providing you platform visibility.
Understand how Isovalent is dedicated to continually bettering the open source communities not just with Cilium!
How to deploy Cilium and Egress Gateway in Azure Kubernetes Service (AKS)
In this blog post, we explore why Isovalent and Cilium power some of the largest AI cloud infrastructures.
In this post, learn about Isovalent Lab Champion program!