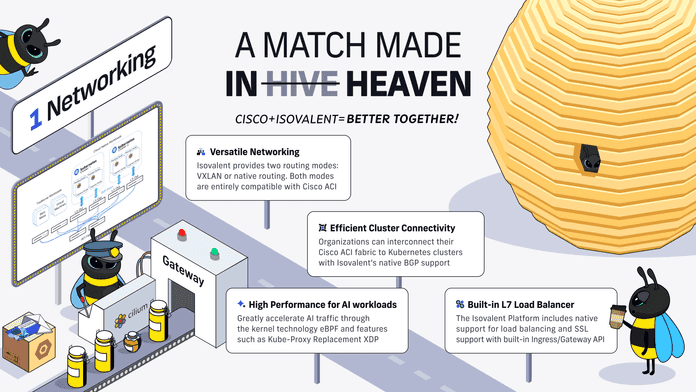
Isovalent & Cisco ACI: Better Together
In this blog post, learn why Isovalent and ACI work so well together to provide enhanced networking, security and observability for K8S!

In this blog post, learn why Isovalent and ACI work so well together to provide enhanced networking, security and observability for K8S!
Dive into Isovalent Enterprise for Cilium 1.16, which includes advanced features like per-flow encryption, Hubble Timescape Lite, and enhanced BGP support for Kubernetes environments.
With Isovalent Enterprise for Cilium, you can leverage BFD to detect defective links and avoid long convergence times.
Discover how to provide micro-segmentation for virtual machines with Kubernetes using Isovalent Enterprise for Cilium and KubeVirt.
This tutorial will guide you through setting up Isovalent Cilium Enterprise’s Cluster Mesh with overlapping Pod CIDR.
Isovalent Enterprise for Tetragon 1.14: Persistent Enforcement, Memory Optimizations, Full Process Visibility, and more!
We think, innovate, and breathe open source and we are fully committed to its principles and values.
Join our communityAdobe achieves a boring network with Isovalent and Cilium, but boring is good!
We show that eBPF is Turing complete, which means it can be used for any computable problem
Learn how Roche worked with Isovalent and deployed Cilium Service Mesh to improve Medical Device Management at the Edge.
See the top eBPF runtime security use cases, and how eBPF security offers stronger runtime enforcement and detection.
In this blog post, learn about how to write your own container network interface from scratch.
Tetragon is the standard for eBPF-based security observability, let’s look at what that means for the top use cases being solved.